The animated map, from an anonymous researcher, is beautiful, mesmerizing ? and made using highly illegal means
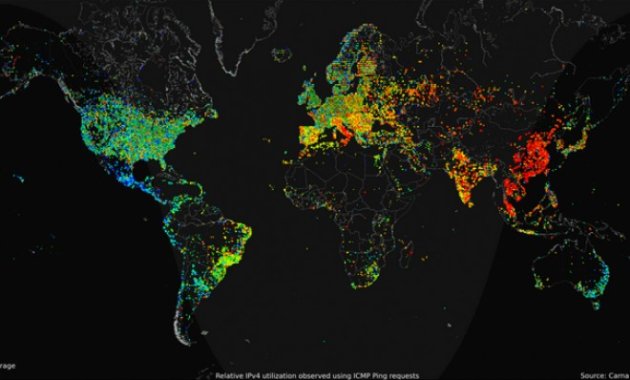
Behold, the internet. In about eight seconds, you can watch a whole day's worth of internet activity around the world, with the higher activity in reds and yellows and the wave shape showing where its day and night. The map was put together by an anonymous researcher in a self-styled "Internet Census 2012." Why isn't he or she taking credit for this remarkable feat of cyber-cartography? The data came from infecting 420,000 computers with automated, web-crawling botnets ? and "hacking into 420,000 computers is highly illegal," says Adam Clark Estes at Vice.
SEE MORE: Will Congress actually break up 'too big to fail' banks?
What are we actually seeing, and how sketchy is its provenance? The researcher, using the 420,000 infected devices, tried to figure out how many of the world's 3.6 billion IPv4 (Internet Protocol version 4) addresses are active; roughly speaking, he got responses from 1.2 billion devices around the world. The map shows the average usage of each device each half hour.
The map isn't totally comprehensive: His botnet, called Carna (after "the Roman goddess for the protection of inner organs and health"), only infected Linux-based devices with some user name?password combination of "root," "admin," or nothing. Also, the world is slowly switching to IPv6, and Carna doesn't measure those devices ? in fact, he says, "with a growing number of IPv6 hosts on the internet, 2012 may have been the last time a census like this was possible." At the same time, "this looks pretty accurate," HD Moore, who used ethical and legal means to conduct a similar survey of smaller scope but larger timeframe, tells Ars Technica.
SEE MORE: Girls on Film: Can the Veronica Mars movie make up for the show's mistakes?
That said, it's a snapshot of 2012, with a limited shelf life. "With cheap smartphones taking off in Africa and $20 tablets popping up in India, the world is becoming more connected by the minute," says Vice's Estes. "So in a few years' time that confetti-colored map of the world above will look less like a chart of privilege and more like an acid trip of progress."
As for the ethics of this census, let's call it "interesting, amoral, and illegal," says Infosecurity Magazine.
SEE MORE: Gun control: Why the fight over universal background checks is the key
The [botnet] binaries he developed and deployed ? it's difficult to call them malware since they had no mal-intent; but it's difficult not to call them malware since they were installed without invitation ? were designed to do no harm, to run at the lowest possible priority, and included a watchdog to self-destruct if anything went wrong. He also included a readme file with "a contact email address to provide feedback for security researchers, ISPs and law enforcement who may notice the project." [Infosecurity]
And if we're being charitable, you could argue that he performed a public service by highlighting how poorly protected our computers, routers, and other internet-connected devices are. Here's a "crude physical analogy" for what the researcher did, says Michael Lee at ZDNet: By himself, he would have been like "a burglar who walks from house to house in a neighborhood, checking to see whether anyone has forgotten to put a lock on their door."With an opportunistic attack, given enough "neighborhoods" and enough time, one could potentially gain an insight into how poorly protected people are. However, with the burglar being a single person, doing so would take them a prohibitively long time ? unless, theoretically, they were able to recruit vulnerable households and send them to different neighborhoods to do the same.... The Carna botnet... highlighted just how many people left their metaphorical front doors unlocked by using default passwords and user logins. [ZDNet]
Still, if this researcher were caught in the U.S., he'd "likely be slapped with one violation of the Computer Fraud and Abuse Act for every computer breached and face something like 50 consecutive life sentences for the sum total," says Vice's Estes. "(I'm being sightly facetious here but only slightly.)" So why take that risk? To see if it could be done, basically.SEE MORE: I took photos of a celebrity cheating on his wife. Should I sell them?
Building and running a gigantic botnet and then watching it as it scans nothing less than the whole internet at rates of billions of IPs per hour over and over again is really as much fun as it sounds like. I did not want to ask myself for the rest of my life how much fun it could have been or if the infrastructure I imagined in my head would have worked as expected. I saw the chance to really work on an internet scale, command hundred thousands of devices with a click of my mouse, portscan and map the whole internet in a way nobody had done before, basically have fun with computers and the internet in a way very few people ever will. I decided it would be worth my time. [Internet Census 2012]
View this article on TheWeek.com Get 4 Free Issues of The Week
Other stories from this section:
Like on Facebook?-?Follow on Twitter?-?Sign-up for Daily NewsletterSource: http://news.yahoo.com/watch-24-hours-internet-activity-around-world-8-113700364.html
MLB Playoff Schedule arizona cardinals Big Bird Adam Greenberg Fall Leaves Jim Lehrer 666 Park Avenue
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.